5 stages of cybersecurity according to NIST framework
incognimous.com
July 24, 2024
Overview
NIST(National Institute of Standards and Technology) published by the U.S, develops cybersecurity standards, guidelines, best practices, and other resources to address the needs of U.S. industry, federal agencies, and the broader public. Our efforts encompass both the creation of actionable information for immediate implementation and long-term research that anticipates technological advancements and future challenges.
Certain NIST cybersecurity tasks are dictated by federal laws, executive orders, and policies. For instance, the Office of Management and Budget (OMB) requires all federal agencies to adopt NIST’s cybersecurity standards and guidance for non-national security systems. Additionally, NIST’s cybersecurity initiatives are influenced by the needs of U.S. industry and the general public. It actively engages with stakeholders to set priorities and ensure that the resources tackle the most pressing issues they encounter.
NIST also plays a crucial role in enhancing the understanding and management of privacy risks, many of which are closely tied to cybersecurity.
Key areas where NIST contributes and plans to intensify its focus include cryptography, education and workforce development, emerging technologies, risk management, identity and access management, measurements, privacy, and the development of trustworthy networks and platforms.
Version 1.0 of the NIST Cybersecurity Framework was published by the U.S. National Institute of Standards and Technology in 2014, initially targeting operators of critical infrastructure. In 2017, a draft of version 1.1 was released for public feedback. On April 16, 2018, version 1.1 was officially announced and made publicly available, remaining compatible with version 1.0. Version 2.0 of the framework was published in 2024.
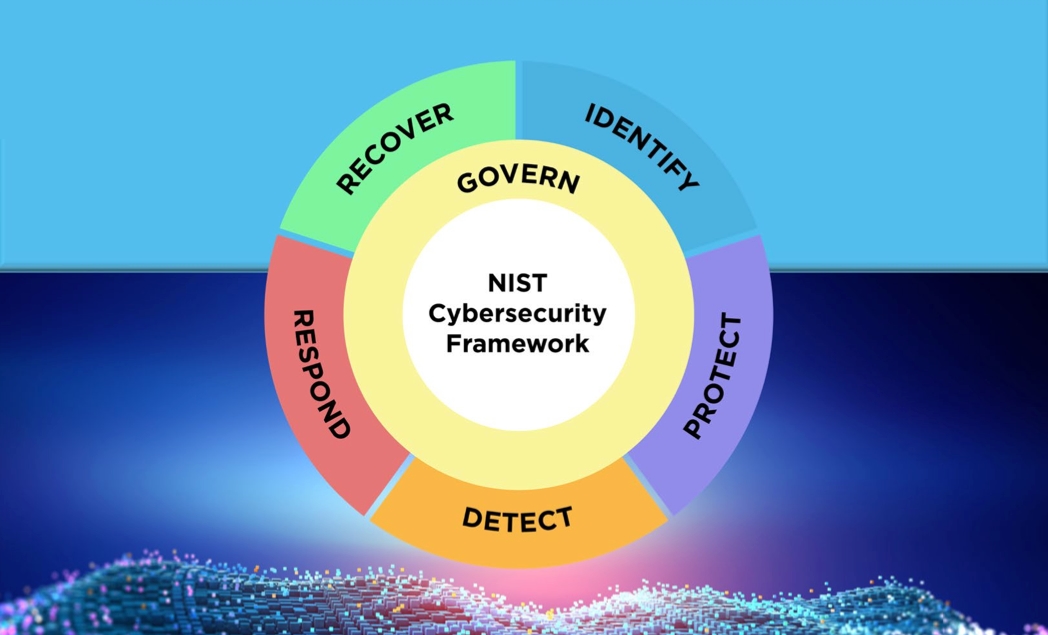
NIST Cybersecurity Framework core structure
The NIST Cybersecurity Framework is structured into functions, categories, subcategories, and informative references.
Functions offer a broad overview of best practice security protocols. They are not meant to be step-by-step procedures but are designed to be carried out “concurrently and continuously to create an operational culture that addresses the evolving cybersecurity risk.”
Categories and subcategories break down these functions into more specific action plans tailored for particular departments or processes within an organization.
Examples of functions and categories defined by NIST include:
Identify: The Identify function focuses on establishing the foundation for a robust cybersecurity program. It helps organizations develop a comprehensive understanding to effectively manage cybersecurity risks across systems, personnel, assets, data, and capabilities. This function emphasizes the importance of aligning efforts with the organization’s risk management strategy and business priorities.
Key activities within this function include:
- Asset Management: Identifying and managing data, personnel, devices, systems, and facilities critical for achieving organizational objectives, aligned with their importance and the organization’s risk strategy.
- Business Environment: Understanding and prioritizing the organization’s mission, objectives, stakeholders, and activities to inform cybersecurity roles, responsibilities, and risk management decisions.
- Governance: Establishing policies, procedures, and processes to oversee and comply with the organization’s regulatory, legal, risk, environmental, and operational requirements, guiding cybersecurity risk management.
- Risk Assessment: Evaluating cybersecurity risks to organizational operations, assets, and individuals, including considerations for mission, functions, reputation, and image.
- Risk Management Strategy: Defining the organization’s priorities, constraints, risk tolerances, and assumptions to guide operational risk decisions effectively.
- Supply Chain Risk Management: Establishing strategies and processes to identify, assess, and manage supply chain risks, aligning with the organization’s priorities, constraints, risk tolerances, and assumptions.
Protect: The Protect function defines necessary measures to safeguard critical infrastructure services and mitigate potential cybersecurity threats.
Key activities within this function include:
- Access Control: Restricting access to assets and associated facilities to authorized users, processes, or devices, and to authorized activities and transactions.
- Awareness and Training: Educating the organization’s personnel and partners on cybersecurity awareness and ensuring they are adequately trained to fulfill their information security-related duties and responsibilities in line with established policies, procedures, and agreements.
- Data Security: Managing information and records (data) according to the organization’s risk management strategy to uphold the confidentiality, integrity, and availability of information.
- Information Protection Processes and Procedures: Maintaining and utilizing security policies, processes, and procedures that define the purpose, scope, roles, responsibilities, management commitment, and coordination among organizational entities to safeguard information systems and assets.
- Maintenance: Conducting maintenance and repairs of industrial control and information system components in adherence to established policies and procedures.
- Protective Technology: Managing technical security solutions to ensure the security and resilience of systems and assets in accordance with applicable policies, procedures, and agreements.
Detect: Detecting potential cybersecurity incidents is pivotal, and this function lays out essential steps to promptly identify any occurrence of a cybersecurity event.
Critical activities within this function encompass:
- Anomalies and Events: Timely detection of anomalous activities and understanding the potential impact of events.
- Security Continuous Monitoring: Monitoring information systems and assets at regular intervals to identify cybersecurity events and assess the efficiency of protective measures.
- Detection Processes: Maintenance and testing of detection procedures to ensure timely and thorough awareness of anomalous events.
These initiatives are essential for organizations to swiftly identify and respond to cybersecurity threats, thereby mitigating risks and safeguarding operational continuity.
Respond: The Respond function centers on executing appropriate actions following the detection of a cybersecurity incident, aimed at containing its impact.
Key activities within this function include:
- Response Planning: Implementing and maintaining processes and procedures to ensure prompt response to identified cybersecurity events.
- Communications: Coordinating response efforts with relevant internal and external stakeholders, including support from law enforcement agencies when necessary.
- Analysis: Conducting assessments to ensure effective response and support subsequent recovery efforts.
- Mitigation: Executing actions to contain and mitigate the impact of incidents, preventing further escalation.
- Improvements: Enhancing organizational response capabilities by integrating insights gained from current and past detection and response activities.
Recover: The Recover function outlines essential activities aimed at revitalizing and maintaining resilience plans to restore any capabilities or services affected by a cybersecurity incident. Emphasis is placed on achieving prompt recovery to normal operations to minimize the impact of cybersecurity incidents.
Key activities within this function complement those of Respond and involve:
- Recovery Planning: Implementing and maintaining recovery processes and procedures to ensure prompt restoration of systems or assets affected by cybersecurity events.
- Improvements: Enhancing recovery planning and processes by integrating insights from past incidents into future activities.
- Communications: Coordinating restoration efforts with internal and external stakeholders, including coordinating centers, Internet Service Providers, system owners, affected parties, other Computer Security Incident Response Teams (CSIRTs), and vendors.
Evolution towards CSF 2.0
The NIST Cybersecurity Framework is designed as a dynamic document, continually updated to reflect advancements in technology and emerging cybersecurity threats. Since the release of version 1.1 in 2018, stakeholders have actively provided feedback on the need for updates. In February 2022, NIST initiated a request for information to enhance the framework, followed by a concept paper in January 2023 outlining proposed revisions. Most recently, NIST introduced the Discussion Draft: The NIST Cybersecurity Framework 2.0 Core with Implementation Examples, inviting public comments until November 4, 2023
Key Revisions
Significant Updates in the Framework from Version 1.1 to 2.0:
- The framework’s title has transitioned from “Framework for Improving Critical Infrastructure Cybersecurity” to simply “Cybersecurity Framework”.
- The framework’s scope has been expanded to accommodate a broader array of organizations that utilize it.
- New implementation examples have been included to offer practical, actionable processes to assist users in achieving CSF subcategories.
- Profiles within the framework have been revised and expanded to showcase diverse profile purposes.
- A new Function, Govern, has been introduced to provide organizational context and outline roles and responsibilities in developing cybersecurity governance models.
- Within this new Function, an additional category focusing on cybersecurity supply chain risk management has been incorporated.
- The update emphasizes cybersecurity assessments, emphasizing continuous security enhancement through a new Improvement Category in the Identify Function.
Recent Posts
-
 The Chaos of Undefined Boundaries: When Work Feels Like the Wild West12 Dec 2024
The Chaos of Undefined Boundaries: When Work Feels Like the Wild West12 Dec 2024 -
 The Real Price of a Late Bug: A Cautionary Tale12 Dec 2024
The Real Price of a Late Bug: A Cautionary Tale12 Dec 2024 -
 Understanding Data Breaches: What Businesses Need to Know10 Dec 2024
Understanding Data Breaches: What Businesses Need to Know10 Dec 2024 -
 What is a pretexting social Engineering Scam? Definition, Attack types and prevention tips09 Dec 2024
What is a pretexting social Engineering Scam? Definition, Attack types and prevention tips09 Dec 2024
Have Any Question?
Connecting with Incognimous Labs means opening the door to advanced cybersecurity solutions tailored to your needs. Whether you have specific concerns, inquiries, or are interested in receiving a quote, we’re here to assist. Use the contact form to briefly describe your requirements, and one of our cybersecurity specialists will get back to you promptly. Take the first step towards a more secure and cost-effective future—reach out now.
- +11 47510964
- connect@incognimous.com
